RouterOS default configuration or residual configurations, as some Mikrotik experts call it, are lines of preconfigured commands on Mikrotik routers that are there to make your job as an administrator easier.
These configurations include commands for fasttrack; a feature in RouterOS that speeds up connections, firewall rules that protect the router from external aggressors, NAT rules and dhcp server for LAN users. Because of Routeros default configuration, an administrator can simply plug in a broad band connection from an ISP and, with little or no configuration on the Mikrotik router, connected users behind the router can access the internet. It makes the job easier. Isn’t it? Is this really a good practice? Why did Mikrotik do this? Read on.
Since Mikrotik have realized that not all organizations are willing to employ an in-house IT officer who is saddled with the responsibility of configuring all network devices including routers, they resolved to simplify the task for these organizations by making sure that RouterOS default configuration is embedded on all Mikrotik small-office/home-office devices. These devices include RB750, RB950, some Mikrotik SXT series, etc. RouterOS default configuration commands are slightly different across selected Mikrotik routers.

RouterOS default configuration in firewall
The firewall sub menu on a Mikrotik router houses the most important part of the RouterOS defualt configurations and as such, will be focused on in this post. The commands here, though meant to make your job easier, can complicate things for you if you do not understand the functions of each rule. I will go over some of the firewall filter rules included in the residual configuration on Mikrotik RB951Ui and explain the advantages/disadvantages. At the end, the system requirement determines what rule should stay or go.
Accept established, related, and untracked connections
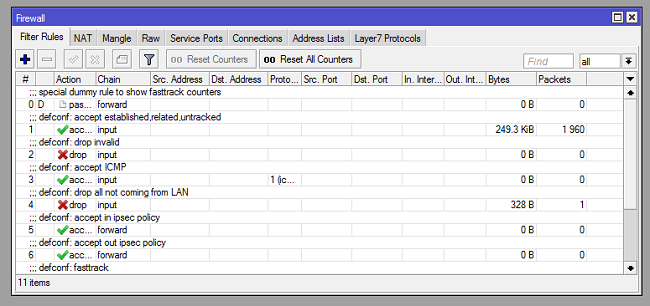
/ip firewall filter add
chain=input action=accept connection-state=established,related,untracked
chain=forward action=accept connection-state=established,related,untracked
This filter rule speeds up connections by ensuring that vetted and established connections to/through the router should not go through the vetting processes again. Likewise, all connections related to these connections (established), should as well be allowed to come in or go through without vetting. Untracked connections (more like VIPs with diplomatic passports) should also be allowed to go through. Doing this speeds up the connections and also reduces processor overhead on the router. This rule is configured for both input and forward chain which means it works on connections to and through the router.
Drop all invalid connections
/ip firewall filter add
chain=input action=drop connection-state=invalid
chain=forward action=drop connection-state=invalid
This firewall filter rule ensures that all invalid connections from any destination to the router and from any destination through your router to other destinations are dropped. If your router is assigned a public IP and you enabled “allow remote dns request “, the rule will help prevent your router from being used as a dns server by users outside your network. I need not tell you that one of the consequences of having your router used as a public dns server is high upload traffics on your network which can bring your network to its knees. I recommend keeping this rule. Invalid connections from your LAN to any destination are also blocked by this rule. The rule comes in both input and forward chain.
Accept ICMP
/ip firewall filter add
chain=input action=accept protocol=icmp
This filter rule ensures that ICMP requests from any location to the public IP on the WAN port of the router are successful. If you want to monitor your router from a remote location through the use of pings, I recommend you keep this rule, especially when the routerOS defualt configuration rule that blocks all requests to the router via the WAN port is enabled. To eat your cake and have it, you can modify this rule to allow selected source IPs. This way, you alone will be able to monitor the router via icmp.
See how to deny icmp request to the public IP on your mikrotik router.
Drop all not comming from LAN
/ip firewall filter add
chain=input action=drop in-interface-list=!LAN
This rule, just like the name goes, drops all requests that are not sourced from the LAN to the router. It helps protect your router from being hijacked by cyber criminals. Perfect, if you do not want to administer your router remotely otherwise, you either disable or modify it. I go with the latter. Create a source address-list with allowed source IP addresses and except the list from the rule. See how to create manual and dynamic address list on Mikrotik.
Accept in and out Ipsec policies
/ip firewall filter add
chain=forward action=accept ipsec-policy=in,ipsec
chain=forward action=accept ipsec-policy=out,ipsec
Mikrotik have realized the challenges faced when trying to enable ipsec vpn connection through a router with firewall filter rules. So, they included this rule to allow ipsec connections through the router even when connections to the router via the WAN port is disallowed. Knowing that ipsec connection will be established using the public IP on the same WAN port to which connections from the internet is disallowed, makes this rule interesting. Kudos to Mikrotik on this one. This rule is worth keeping, though can be modify by allowing connections only from the remote ipsec peer.
Fasttrack
/ip firewall filter add
chain=forward action=fasttrack-connection
The fasttrack rule is a forward chained filter rule that allows established, related, and untracked connections to be fast-tracked. I have written a post on fasttrack. See Mikrotik fasttrack rule and why you need to enable it.
Drop all from WAN not DSTNATed
/ip firewall filter add
chain=forward action=drop connection-state=new connection-nat-state=!dstnat in-interface-list=WAN
This rule is a smart one. Mikrotik has realized that users often use destination NAT to allow locally hosted resources to be accessed over the internet through the public IP address assigned to the Mikrotik router. To help correct the vulnerabilities that comes with such practices, they included this rule in routeros default configuration.
The rule ensures that requests to the WAN port on destination ports that are not used for NAT are dropped. I recommend keeping this rule. See here for how to configure destination nat also known as port-forwarding on Mikrotik.
In conclusion, I will say keep the routeros default configuration of you understand its functions and can modify it to meet your requirements.
If you enjoyed this tutorial, please subscribe to this blog to receive my posts via email. Also subscribe to my YouTube channel, like my Facebook page and follow me on Twitter.

/ip firewall filter add
chain=forward action=drop connection-state=invalid
chain=forward action=drop connection-state=invalid
The first one should be chain-input, I think…
From my experience, the first one is input. That is for connection to the router. The second is forward: connections through the router.
We agree and say the same. But the text show the “same” command for both entry. Like a cut and paste without modifying the “forward” to “input” of the first command.
It was an error on my part. It has now been corrected. Thank you.
why do we need to accept input established,related,untracked? Once I enable it then icmp limiting “2p/second” doesn’t work (as it’s probably related connection).
/ip firewall filter add
chain=input action=accept connection-state=established,related,untracked
Established and related connection is meant to speed up the transmission of packets for already established connections. By exempting these packets from regular checks, the system ensures that packet are transmitted fastly.
Mikrotik HEX with 7.3 router OS had the rule “Drop all invalid connections” active for LAN as default.
This seemed to be the cause for TP-link wlan controller (omada) not to be able to connect to access points. I am guessing same could apply to other wifi solutions as well.
I changed the rule to WAN, since it was supposed to prevent outsiders from using the router as DNS.
Thanks for good explanations for first time user of Mikrotik!