If you have a Mikrotik router that has been assigned a public IP, making sure that your router is protected by blocking port access to it from the internet is non-negotiable. You must ensure that both UDP/TCP ports that can be used to infiltrate your router and wreak havoc on your network are blocked, especially to users on the internet who may want to attack your network.
In this demonstration, I will share with us on how to block ftp, snmp, telnet, ssh, http, https, etc, access to your router from the internet. The beautiful thing about Mikrotik, which a privilege few know, is that with Mikrotik, you do not need to install a firewall device to protect your network as the Mikrotik router itself is a firewall device, and when properly configured, can protect itself as well as LAN users connected behind it. Let’s consider the network topology below:
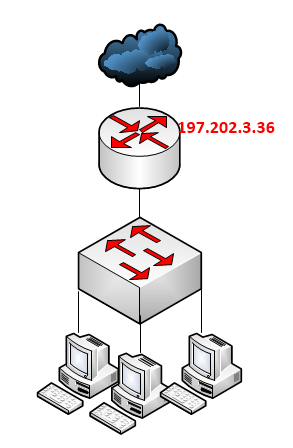
From the image above, our task is clearly defined; protect the router from attacks from the internet by locking down the ports listed above. Since the router has been assigned a public address, as shown on the network topology, it means that the router can be reached from devices connected to the internet. To protect the router, we will configure firewall filter rules to block udp/tcp ports access to the public address assigned to the router. See below:
Blocking TCP/UDP ports on Mikrotik
First of all, you must understand the following attributes that will be used in the firewall rules.
Destination address = the public IP assigned to the Mikrotik router. If there are more than one public IP on the router, an address-list must be used to capture all public addresses on the router.
Chain = since the access is aimed at the router and not the devices behind the router, the chain is input.
Protocol = tcp or udp, depending on the port number.
Action = drop.
You may also like: How to permit icmp request from the internet to the IP on the WAN interface of your security router
The following firewall filter rules will block http, https, ssh, ftp, telnet, winbox, and snmp ports on the router. This will ensure that anyone trying to use any of these applications to access the router from the internet will be denied access.
ip firewall filter
/add chain=input dst-address=197.202.3.36 protocol=tcp dst-port=21 action=drop
/add chain=input dst-address=197.202.3.36 protocol=tcp dst-port=23 action=drop
/add chain=input dst-address=197.202.3.36 protocol=tcp dst-port=22 action=drop
/add chain=input dst-address=197.202.3.36 protocol=tcp dst-port=80 action=drop
/add chain=input dst-address=197.202.3.36 protocol=tcp dst-port=161 action=drop
/add chain=input dst-address=197.202.3.36 protocol=tcp dst-port=8729 action=drop
/add chain=input dst-address=197.202.3.36 protocol=tcp dst-port=8291 action=drop
Also see: Mikrotik security: How to block icmp requests to the WAN IP on your Mikrotik router
The rules above will block the use of the following application to access the router from the internet:
Ftp(21), telnet(23), ssh(22), http(80), snmp(161), https(8729), and winbox(8291)
Kindly note that the IP address used in this demonstration does not belong to timigate and was only used for demonstration purposes. Attempts to attack this IP, is highly discouraged.
