Security is paramount in networking, that is why Cisco puts extra layer of security on their gateway devices to make sure that traffics originating from the internet to your routers are not allowed in by default. However, using what is known as reflexive access-list or stateful inspection, traffics that originated from your LAN will be allowed in and through the router as they make their way back. In this, I will share how to allow icmp request from the internet to your router.
Recently, one of the questions I was asked bothered on what I just explained. The reader wants to know how to permit icmp requests originating from the internet to his router. In this demonstration, I will share with us a simple way to accomplish this.
Before I proceed, let’s look at why you may want to allow icmp request from the internet to your router. Simply put; for monitoring purpose. Some of the network tools used for monitoring network nodes make use of icmp as one of the polling agents used in determining node reachability/availability. With icmp requests to an internet-based device turned off, determining device availability becomes difficult, if not impossible.
Most security devices make use of stateful firewall inspection technique to keep track of network connections. These connections include TCP streams and UDP communication, making sure that significant amount of these attributes are kept in memory. With this, the router is able to monitor incoming and outgoing packets, as well as the state of the connection and allow filtering decisions to be made based on rules defined by the administrator as well as packets belonging to previously established connections
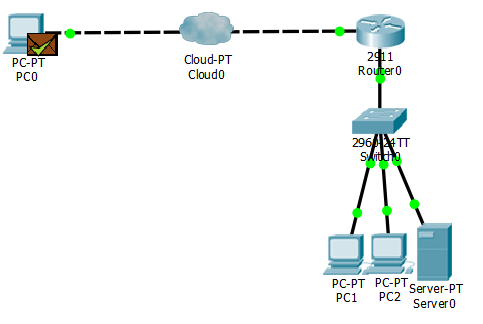
Network Topology
Configurations
One of the ways to allow icmp requests from the internet to the public IP on the route is through the use of access-list. In this example, I will use an extended access-list to permit icmp requests from any host on the internet to the router while denying all forms of access from the internet to the router through the WAN port. The commands are simple and straight forward. See code below.
Router0(config)#ip access-list extended allow-icmp
Router0(config-ext-nacl)#permit icmp any host 196.252.244.x
Router0(config-ext-nacl)#deny ip any host 196.252.244.x
Router0(config-ext-nacl)#exit
Router0(config)#int g0/0
Router0(config-if)#ip access-group allow-icmp in
Verification
To verify the configuration, I will send icmp packets from PC0 to the IP on the WAN port of Router0, after that, I will try to initiate a telnet session from the same PC to the router. While the icmp requests are expected to be successful, the telnet session should not. See results in the image below.

Thanks for ready and please feel free to drop your questions in the comment box below.

What happens to ssh and telnet requests to the router from the internet, given that this setup denies all other packets from the internet to the router?
The config only permits icmp request from the internet to the router. To allow ssh and telnet, enter two lines of permit statements for port numbers 22 and 23