Connecting branch offices to the HQ can be done in different ways, depending on the requirements of the customer. One of such requirements would be that the routers in both locations be on the same subnet. The customer does not want the existence of hops between both locations. With such requirement, even though there is no direct connection between the locations under consideration, l2tpv3 can be configured to connect both locations and create a virtual connection between locations.
L2tpv3, also referred to as ethernet private line, makes use of UDP protocol 115 and can tunnel any layer2 traffic over the vpn link using IP. In this demonstration, we have two locations, the HQ and the branch office. Our goal is to provide a layer 2 connection between the HQ and BO routers. This setup is used mostly by ISPs to connect branch offices of same company to their HQ. In this demonstration, we will see how it is done. Let’s look at the topology below:
Network Topology

Both ISP PE routers have connections to the core router, which in our network topology is represented by a cloud. I will be using OSPF to ensure but PE routers can reach each other.
What to note
- On both PE routers, no IP addresses will be configured on the interfaces connecting to the customer routers.
- Loopback interfaces will be created on both PE routers for establishing layer 2 tunnel
You may also like: How to successfully configure Cisco site-to-site IPsec VPN in 5 minutes!
Configuring IP addresses and OSPF on the core router
Core(config)#int f0/0
Core(config-if)#interface FastEthernet0/0
Core(config-if)# ip address 10.0.0.1 255.255.255.252
Core(config-if)#description connection-to-PE1
Core(config-if)#no shut
Core(config-if)#interface FastEthernet0/1
Core(config-if)# ip address 20.0.0.1 255.255.255.252
Core(config-if)#description connection-to-PE2
Core(config-if)#no shut
Core(config-if)#exit
Core(config)#router ospf 1
Core(config-router)#network 10.0.0.0 0.0.0.3 area 0
Core(config-router)# network 20.0.0.0 0.0.0.3 area 0
Configure IP addresses and OSPF on ISP Provider Edge router 1
PE1(config)#int f0/0
PE1(config-if)#interface FastEthernet0/0
PE1(config-if)# ip address 10.0.0.2 255.255.255.252
PE1(config-if)#description connection-to-Core
PE1(config-if)#no shut
PE1(config-if)#interface loopback1
PE1(config-if)# ip address 1.1.1.1 255.255.255.255
PE1(config-if)#description L2tpv3-connection-to-PE2
PE1(config-if)#exit
PE1(config)#router ospf 1
PE1(config-router)#network 10.0.0.0 0.0.0.3 area 0
PE1(config-router)# network 1.1.1.1 0.0.0.0 area 0
Configure IP addresses and OSPF on ISP Provider Edge router 2
PE2(config)#int f0/0
PE2(config-if)#interface FastEthernet0/0
PE2(config-if)# ip address 20.0.0.2 255.255.255.252
PE2(config-if)#description connection-to-Core
PE2(config-if)#no shut
PE2(config-if)#interface loopback1
PE2(config-if)# ip address 2.2.2.2 255.255.255.255
PE2(config-if)#description L2tpv3-connection-to-PE1
PE2(config-if)#exit
PE2(config)#router ospf 1
PE2(config-router)#network 20.0.0.0 0.0.0.3 area 0
PE2(config-router)# network 2.2.2.2 0.0.0.0 area 0
Now, we need to be sure that the loop back ip address on PE2 is reachable from PE1
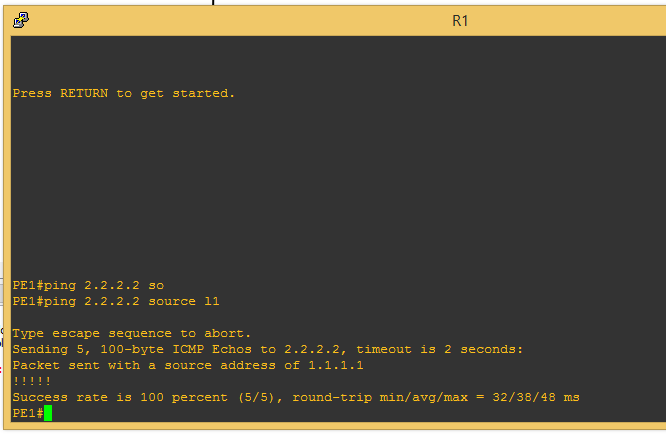
Now that we are certain that we can get to the loopback address on PE2 from the loopback address on PE1, we proceed to configuring L2TPV3.
You may also like: How to configure Mikrotik GRE Tunnel for Site to Site VPN using IPSEC for encryption
Configuring L2TPV3 on PE1
PE1(config)#pseudowire-class pe1
PE1(config-pw-class)#encapsulation l2tpv3
PE1(config-pw-class)# ip local interface Loopback1
PE1(config-pw-class)#exit
PE1(config)#int f0/1
PE1(config-if)#desc connection-to-BO
PE1(config-if)#xconnect 2.2.2.2 20 encapsulation l2tpv3 pw-class pe1
PE1(config-if)#no shut
Configuring L2TPV3 on PE2
PE2(config)#pseudowire-class pe2
PE2(config-pw-class)#encapsulation l2tpv3
PE2(config-pw-class)# ip local interface Loopback1
PE2(config-pw-class)#exit
PE2(config)#int f0/1
PE2(config-if)#desc connection-to-HQ
PE2(config-if)#xconnect 1.1.1.1 20 encapsulation l2tpv3 pw-class pe2
PE2(config-if)#no shut
Please note that the psedowire-class can be any name and I chose to use the hostname of the router. The xconnect address must be the reachable loopback address on the remote routers while the tag can be any number within the allowed range and must be same on both routers. This number is unique to the tunnel and cannot be used on this router for any other tunnel.
On customer routers
On HQ and BO routers, I will only assign IP addresses from the same subnet to the interfaces connecting to the PE routers and try to ping across.
On HQ router
HQ(config)#int f0/0
HQ(config-if)#ip add 192.168.1.1 255.255.255.252
HQ(config-if)#no shut
On BO router
BO(config)#int f0/0
BO(config-if)#ip add 192.168.1.2 255.255.255.252
HO(config-if)#no shut
Verification
Ping the branch office IP from HQ

The ping was successful while the result of traceroute shows that there are not hops in between.
