In this post, I will explain five common configuration mistakes that every Mikrotik routeros user should avoid. These mistakes are so common that you can find at least three of them on 80 percent of all configured Mikrotik routers on the internet.
I have learned over the years that the hardest part of networking is not provioning your routers to connect users to the internet. In fact, it is the easiest. The hardest part lies in securing your routers from external aggressors. Unfortunately, many Mikrotik routeros users pay little or no attention to this part.
Recently, there have been many cases of Mikrotik routers that have been compromised by hacker. I am not surprised by this. If not for anything, it confirms my earlier statement that 80 percent of Mikrotik routers are prone to attacks because the users have failed to avoid these five common mistakes. In addition to these five common mistakes, there are other measures that should be taken to secure your Mikrotik router.
Read: What to do when Mikrotik router displays wrong username or password
Five common mistakes routerOS users make on Mikrotik routeros
1. Using a name for username
Many Mikrotik routeros users make the mistake of using names like admin, superadmin, mikrotikadmin, or their given names as username. If your router has a public IP address configured on it, it is highly unadvisable for you to use any of these names as your username. Hackers who attempt bruteforce attacks against network devices using applications like Cain and Abel, will try multiple passwords together with any of these names
Except when authorization is done on a radius server, the Mikrotik routerOS has no limit on failed login attempts (I stand to be corrected on this), Mikrotik routers are usually seen as soft targets for bruteforce attacks. If possible, make your usernames as strong as your passowords. Use a combination of names and special characters to form a username.
Failed unauthorized login attempts on unsecured Mikrotik routers can bee seen by clicking on log. See image below and note the usernames used.

2. Using weak passwords
While everyone understands the danger of using weak passwords, many Mikrotik routeros users still use them simply because they do not want to configure complicated passwords that can be easily forgotten.
The truth is that passwords can be forgotten if they are not in use. Once set on a router, no matter how complicated, constant login on the router ensures it is not forgotten. Using passwords like admin@12345, p@55w0rd, Protect@123, etc, will not only cause you to be treated like someone who has forgotten the passord to a router, it also ensures that your device is quickly taken over and you, surfer the effect of denial of servce attacks.
Use strong passwords made up of upper and lowercase letters, special characters, etc.
Also read: How to configure Port forwarding through multiple MikroTik Routers
3. Enabling allow remote dns request
By checking the box to allow remote dns request while setting a dns server IP on the router, you are provioning your router to serve as a dns sever to users on your network. The original intention of Mikrotik concerning this routeros feature is to reduce the dns resolution time for users on your network and as a result, speed up browsing experience.
Unfortunately, enabling allow remote request on a Mikrotik router with a public IP address and with no firewall filter rule(s) to secure the router against external dns requests can ground your network. Your router suddenly becomes a public dns server, receiving hundreds and thousands of dns requests from the internet. The two obvious effects of this mistake are high processor utilzation on your router and high upload traffic on your network.
If you don’t want to spend hours troubleshooting the cause of network congestion, enable this feature only when you have a firewall filter rule that drops dns requests coming from the internet on your router.
Also read: How to redirect dns requests on Mikrotik routers
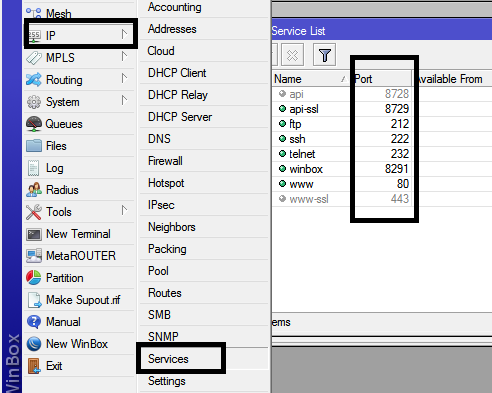
4. Using default port numbers
Part of the reasons unauthorized login attempts are successful on most Mikrotik routers is simply because most users do not change the post numbers from their default values. When popular port numbers are changed, it can serve as the first security layer on the router as the attackers will then have to enter the correct port number, say for ssh, to get to the router before login credentials are required.
For example, if the ssh port is changed from 22 to 9621, the first challenge faced by an attacker will be to get the correct port number which obviously is not as simple as ABC. It is only when the correct ssh port number is used that username and password combinations can be done using bruteforce attack. By stopping the attacks from getting to the router, you save your device some processor utilization.
Apart from changing the port numbers, applications that are not needed should have their ports shutdown.
5. Absence of firewall filter rules
Most Mikrotik routeros users don’t bother going to the firewall section of the router because they feel it is too complicated. As long as the router can provide internet access to connected users, they are okay. Now hear this, if your router is assigned a public IP address, leaving it without a filter rule is not advisable.
Most small office Mikrotik routers like the RB750 series come with preconfigured firewall filter rules that protect the router from external aggressors. Unfortunately, most users with limited or no knowledge of what these rules do often times disable them. On MIkrotik routers like the RB1100 series with no preconfigured firewall rules, users should add at least an input-chained firewall filter rule to protect the router from access via the internet. An example is given below.
ip firewall filter add chain=input in-interface=WAN action=drop
If you enjoyed this tutorial, please subscribe to this blog to receive my posts via email. Also subscibe to my YouTube channel, like my Facebook page and follow me on Twitter.
