Its a new week. Holiday is over, and we back to work. I know. As much as you and I hate to the reminded that its Monday, the truth is, it is. So here we go!
Today, I am going to talk about standard access-list. Access list is a security feature used on routers for a variety of reasons. Ranging from access control, to traffic filtering and so on. Access lists work with wild card masks to determine the range of IP addresses to be matched. There are two main types of access-lists: the standard ACL and the extended ACL. Other categories of ACL like the named ACL can either be standard named ACL or extended named ACL. Today, we consider standard ACL.
Standard access-list is a simple form of ACL that does filtering based on source address only. It does not put into consideration the destination address as well as the port number. What this means is that the standard access-list does not give you the flexibility that the extended access-list affords you. It can be used when configuring NAT as well as a host of other reasons.
Here is an example of standard access-list
(adsbygoogle = window.adsbygoogle || []).push({});
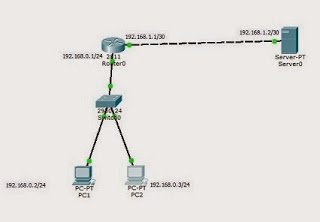
From the above topology, we are going to configure a standard ACL to stop the users on the LAN from getting to the Server. Just before that, lets confirm that we can reach the server:
Good enough, it is reachable. So, lets configure a standard ACL
Router>en
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#access-list 1 deny 192.168.0.0 0.0.0.255
Router(config)#access-list 1 permit any
Router(config)#int f0/0
Router(config-if)#ip access-group 1 out
Router(config-if)#exit
Router(config)#exit
Router#copy run start
Lets see if it worked:
Now, the pings return with destination host unreachable message. Shows our ACL is working!
Guys, there you have it. I hope this helps.




Thats an awesome write up sir,